Quorum Cyber Threat Intelligence Outlook 2024 Report analyzes tumultuous year

By Ken Showers, Managing Editor
Updated 1:12 PM CST, Fri February 23, 2024

EDINBURGH, Scotland – 2024 is set to be a year full of security landmark events and challenges. Looking ahead Quorum Cyber has released its "Threat Intelligence Outlook 2024" report to address these cyber threats.
The in-depth report offers a strategic analysis of emerging cybersecurity threats, from malware and ransomware developments to geopolitical considerations and the outlook for 2024 global events.
Among its topics are examining the “Big Four” nation-state groups. It emphasizes the complex web of geopolitical objectives tied to the activities of nation-state-sponsored groups from the Big Four countries: Russia, China, Iran, and North Korea. A topic made more poignant with the recent dismantling of LockBit, a Russian sponsored Ransomware group.
Another key highlight of the "Threat Intelligence Outlook 2024" report examines the downsides of artificial intelligence (AI). In 2024 AI will include automated phishing and social engineering operations, as well as the utilization of advancing deepfake technologies to sway public opinion and exploit organizations across the industry sector spectrum. These platforms will likely be developed and offered as a service for threat actors to purchase on underground forums and the dark web, according to Quorum Cyber.
The report also examines potential tampering of the upcoming U.S. presidential elections. According to Quorum Cyber, nation-state-sponsored threat actors will almost certainly seek to exert influence to manipulate the U.S. election, with operations likely to include state-level cyber espionage, Information Operations (IO), and impersonation attempts aimed toward both voting systems and civilian voters. Moscow will likely seek to leverage cyber-IO to promote candidates sympathetic to Russia’s foreign policy objectives, the report said, a main priority being disrupting U.S. support for the current Ukrainian President, Volodymyr Zelensky.
“Being proactive means constantly looking ahead to scan for any threats looming over the horizon - something that our Threat Intelligence team excels in,” said Federico Charoksy, CEO & founder of Quorum Cyber. “The Quorum Cyber Threat Intelligence Outlook 2024 provides a clear picture of the threat landscape for the months ahead and gives readers valuable insight into how we’re working to head off cyber threats.”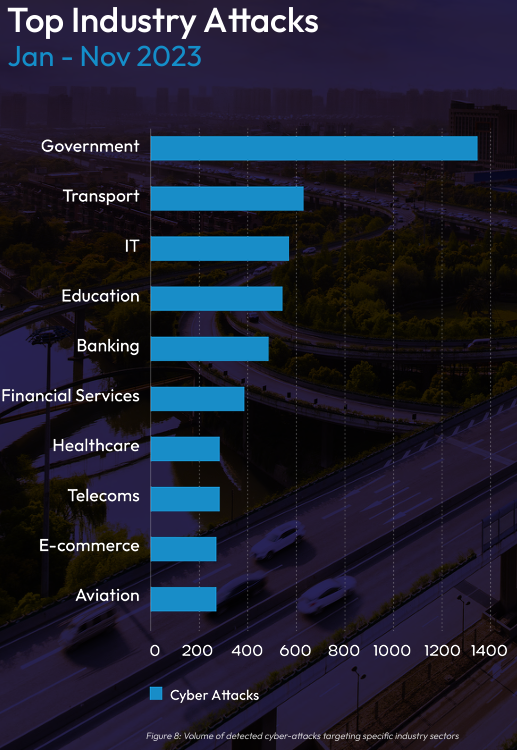
Security Systems News (SSN) reached out to the experts at Quorum Cyber to dig into some of the finer points of the report. We asked if they expect any seismic shifts in the spread of industry attacks in 2024 based on the chart in the report (page 59), and if industries are at the higher end of the graph because they have not been subjected to the same data privacy and security regulations as other industries (as the report implies of the education sector).
“It is likely that the distribution of industry attacks will observe some changes as the calendar year progresses,” said Craig Watt, Quorum Cyber threat intelligence consultant. “Firstly, we expect the financial and banking sectors to be subjected to a higher volume of cyberattacks as a result of several factors, including:”
- The targeting profile of Iranian state-sponsored cyber threat actors likely expanding to include these sectors in response to continuing economic sanctions following the ‘Transition Day’ of the Joint Comprehensive Plan of Action (JCPOA).
- North Korea-aligned cyber threat actors likely ramping up financial and banking sector targeting in response to ongoing economic sanctions, as external trade continues to be severely limited.
- Nation-state threat actors likely pivoting to zero-day vulnerability exploitation against the sectors as a substantial portion of financial and banking entities depend on third-party software supply chains for their business procedures.
- Secondly, we also expect the technology sector to be subjected to a higher volume of cyberattacks due to the following factors:
- Chinese nation state-sponsored cyber operations likely being launched against the sector with the objective of disrupting the critical national infrastructure (CNI) of rival states that rely on technology solutions for their operational protocols.
- A likely spike in influence operations (IO) as threat actors seek to interfere with and disrupt high-profile political elections throughout 2024 by leveraging AI technologies allowing for scaled campaigns, resulting in social tensions and the erosion of confidence in political institutions.
He continued, “Industries at the higher end of the graph do not necessarily represent these organizations being subjected to less data privacy and security regulations. For instance, the government sector is at the top of the list in terms of industry attacks for a number of reasons that are not directly related to data privacy regulations, including:”
- As the geopolitical landscape continues to remain fractured and the requirement for nation state-level espionage surges, government organizations are a priority target resulting from the storage of a significant quantity of sensitive data relating to citizens.
- Significant levels of hacktivist targeting against government entities are launched with the objectives of protesting against opposing government policies that will inevitably continue to be drafted in high volume.
- Nation state-level threat actors targeting rival government entities with the objective of understanding foreign policies regarding ongoing conflicts.
“Additionally, the technology sector is toward the top of the list in terms of industry attacks for a number of other reasons including:”
- Organizations across the industry spectrum being dependent upon IT functions means that technology firms will almost certainly be targeted by cyber threat actors as the sector is critical to national security, economy, and public healthcare.
- The technology sector has a high-risk appetite with open testing environments, as well as the early adoption of new technologies, thus increasing the attack surface available for threat actors to target.
- As businesses increasingly rely on cloud-based solutions, threat actors will likely target the sector with attempted exploitation of cloud vulnerabilities.
SSN also asked Watt what was the best protection for businesses worried about ransomware attacks as a result of zero-day exploits. “As ransomware is the most common malware payload deployed through the exploitation of zero-day security flaws, it is critical for businesses within the public and private sectors to bolster their security defenses to prevent potential ransomware compromise,” he said. “Malicious cyber actors can execute their ransomware payloads by exploiting zero-day exploits in target systems. Recommended mitigation strategies include:”
- Routinely apply security patches regarding products used for data backups, so that threat actors cannot exploit any known vulnerabilities that may exist.
- Patch any known vulnerabilities in remote access and external facing devices as ransomware operators increasingly access target networks remotely via exposed services.
- Install security updates as soon as they become available to secure vulnerable products
- Enable automatic updates for operating systems, applications, and firmware
- Use the latest versions of operating systems and applications that have the most up-to-date security features
- Configure host and network-based firewalls and block inbound connections
The complimentary report is available courtesy of Quorum Cyber online at www.quorumcyber.com.
Comments